
I had the pleasure of recently conducting a timely webinar on the Top Five Ways to Secure All Remote Workers with two executives from our partners at Microsoft – – Dave Randall, Senior Program Manager of Endpoint Manager, and Aasawari Navathe, Program Manager.
The world changed overnight
Even before the pandemic, it’s surprising how quickly IT needs and our world has changed. Think back a few years, many employees were sitting at a desktop with a LAN connection. The company firewall was the security perimeter and effectively all your resources were on-premise.
As companies were improving flexibility of the workspace, we saw a shift to laptops and tablets as a primary work device, where users and devices were no longer behind the firewall. SaaS apps and services meant users were connecting over the internet to get work done.
And now we find ourselves in a very accelerated trajectory to embrace zero trust principles and deploy tools that support them – because foundationally, they are what help your organization protect itself while allowing users to remain productive in this new work from home environment.
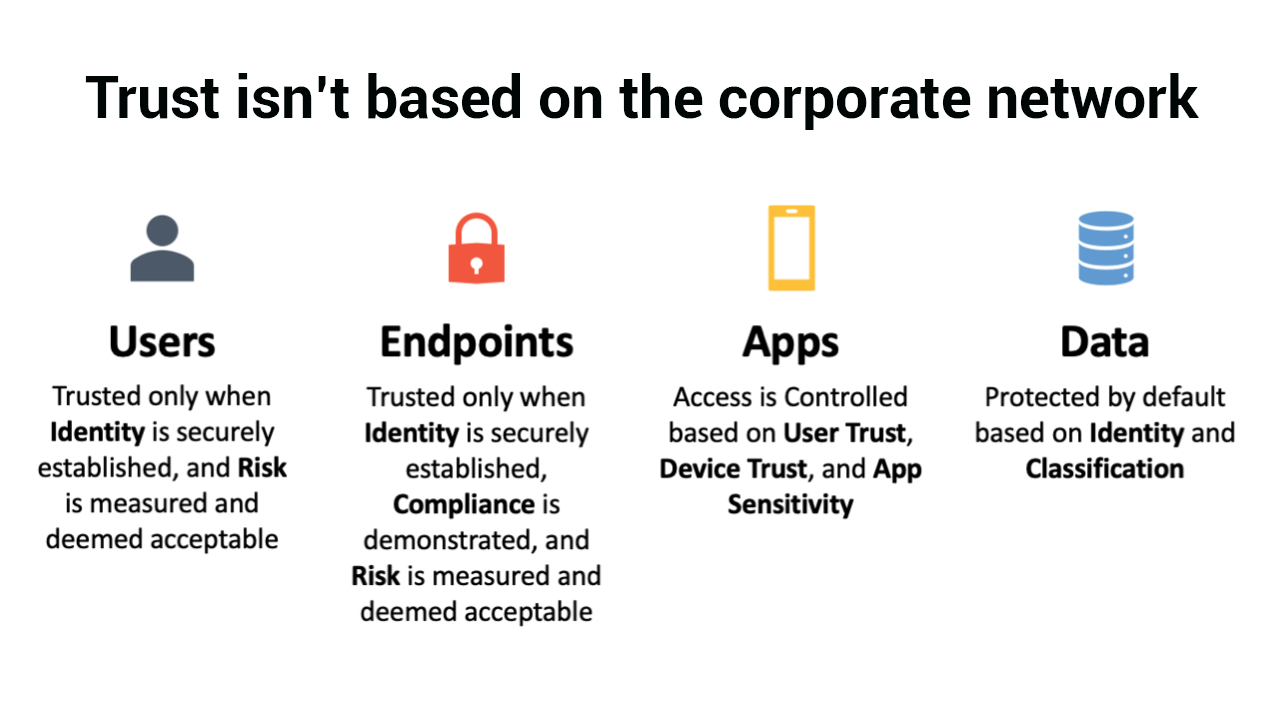
From a security perspective we, by default, don’t trust any user, endpoint, app or data. Each of these four elements need to gain our trust. And the system helps you prescribe rules to establish what’s trusted, and what happens when any of the elements don’t meet those rules.
If you were on the path to supporting these zero trust initiatives, you likely had a solid plan and timeline in place. But, with the arrival of COVID-19, that was likely interrupted and a crisis plan of respond/recover/rebuild took its place.
Many of you are still in the respond “work from home mandates” phase. Quick shifts in your IT initiatives and support can’t come at the expense of your long term goals, either with increases in cost, or greater risks. And further down the road you’ll be rebuilding to ensure a new normal represents your vision of organizational security and productivity.
With this in mind, here are our Top Five Ways to Secure All Remote Workers:
1 – Manage corporate endpoints with Microsoft Endpoint Manager MDM
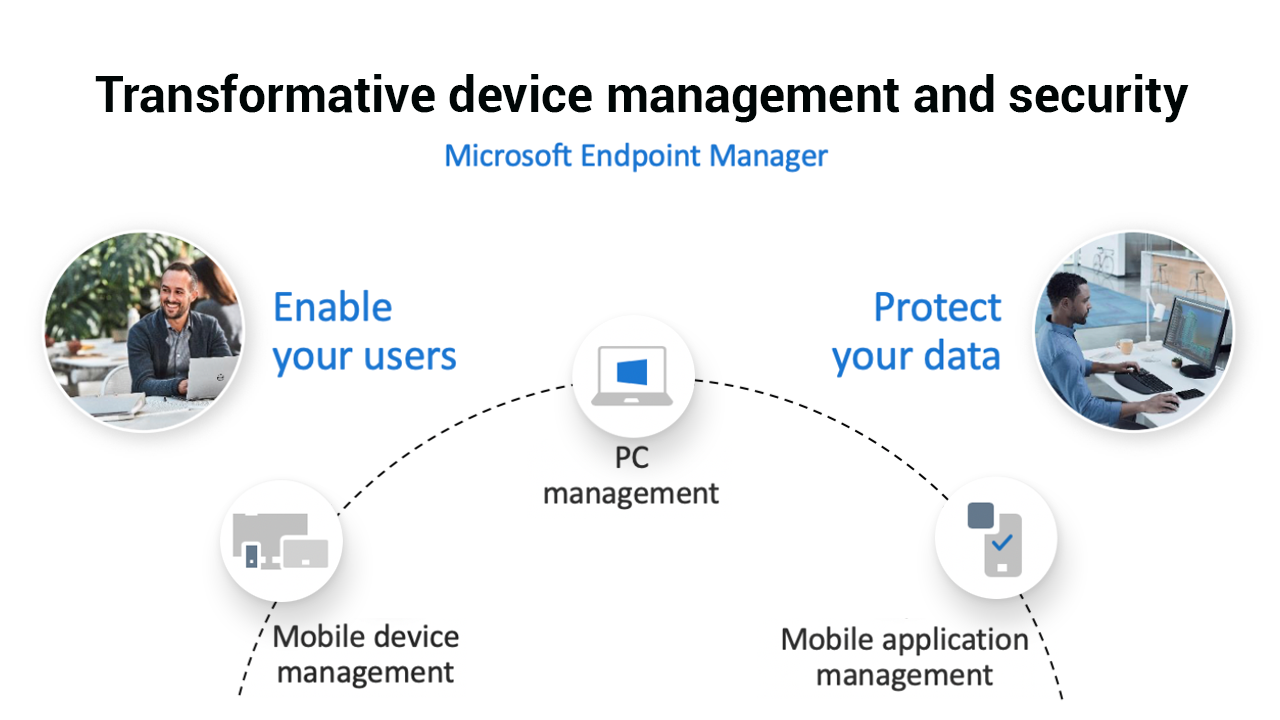
We want to begin with a solid foundation to build from – Microsoft Endpoint Manager. Microsoft Endpoint Manager helps focus on outcomes:
- Are the right people on the right devices accessing the right information?
- Is the data protected at all times?
- Is the system automatically detecting and responding to any threats, whether internal or external?
- Are the applications you use to access data protected with policies?
- Are my corporate PC’s, and mobile devices manageable from one location to ensure consistency in security and policy across all platforms?
 With Microsoft Endpoint Manager – and as a solution that brings together Configuration Manager and Intune – you’re in a position to answer yes to those previous questions, and that’s a strong position to come from.
With Microsoft Endpoint Manager – and as a solution that brings together Configuration Manager and Intune – you’re in a position to answer yes to those previous questions, and that’s a strong position to come from.
2 – Secure your traditional corporate endpoints with Microsoft Endpoint Manager and Defender ATP
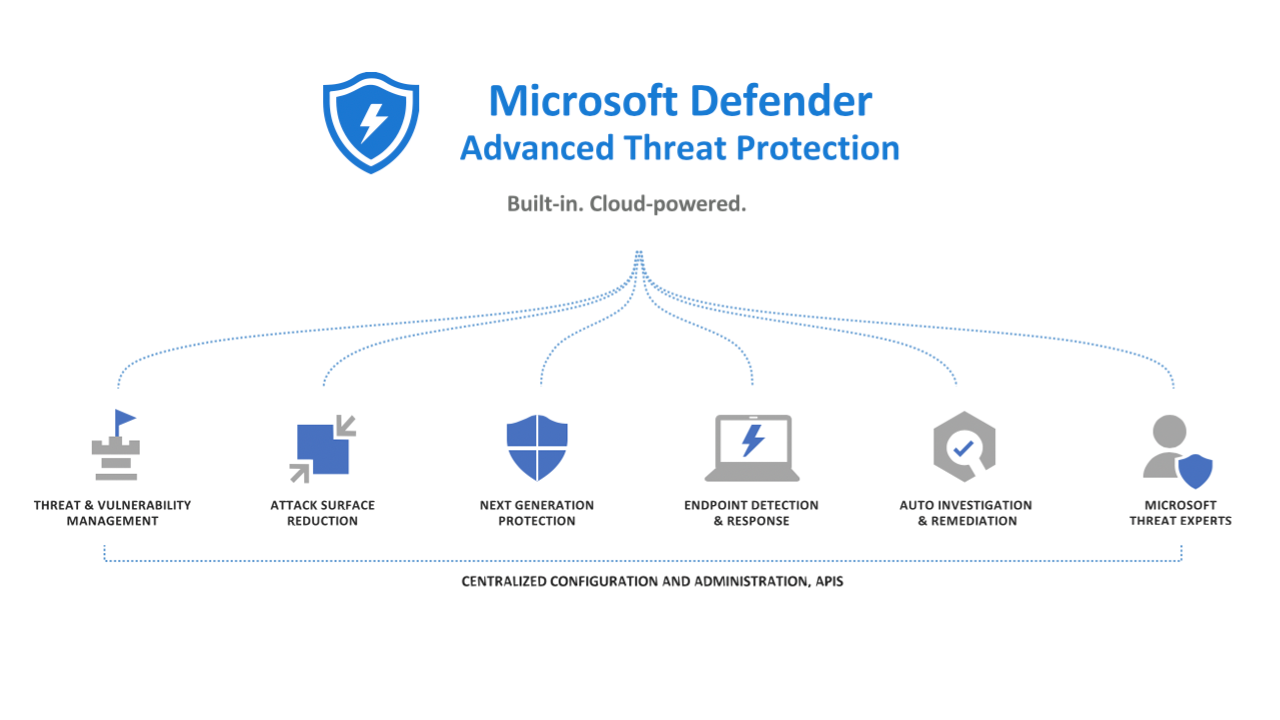 Defender ATP resides within the Microsoft Endpoint Manager console, where settings can be configured and deployed. From one location, you have a consistent view of your security configuration, as well as a place to deploy settings to both your cloud connected and on-premises PC’s.
Defender ATP resides within the Microsoft Endpoint Manager console, where settings can be configured and deployed. From one location, you have a consistent view of your security configuration, as well as a place to deploy settings to both your cloud connected and on-premises PC’s.
3 – Secure your corporate mobile endpoints with Zimperium zIPS
Typically, companies are much more proactive in protecting PCs while mobile devices often go unmonitored and unprotected. While mobile platforms have some built-in protection such as app container isolation and vetted consumer app stores, these platforms remain vulnerable to attacks.
As more employees use devices for work and to access sensitive data, the information from mobile threat defense (MTD) solutions can help protect devices and resources.
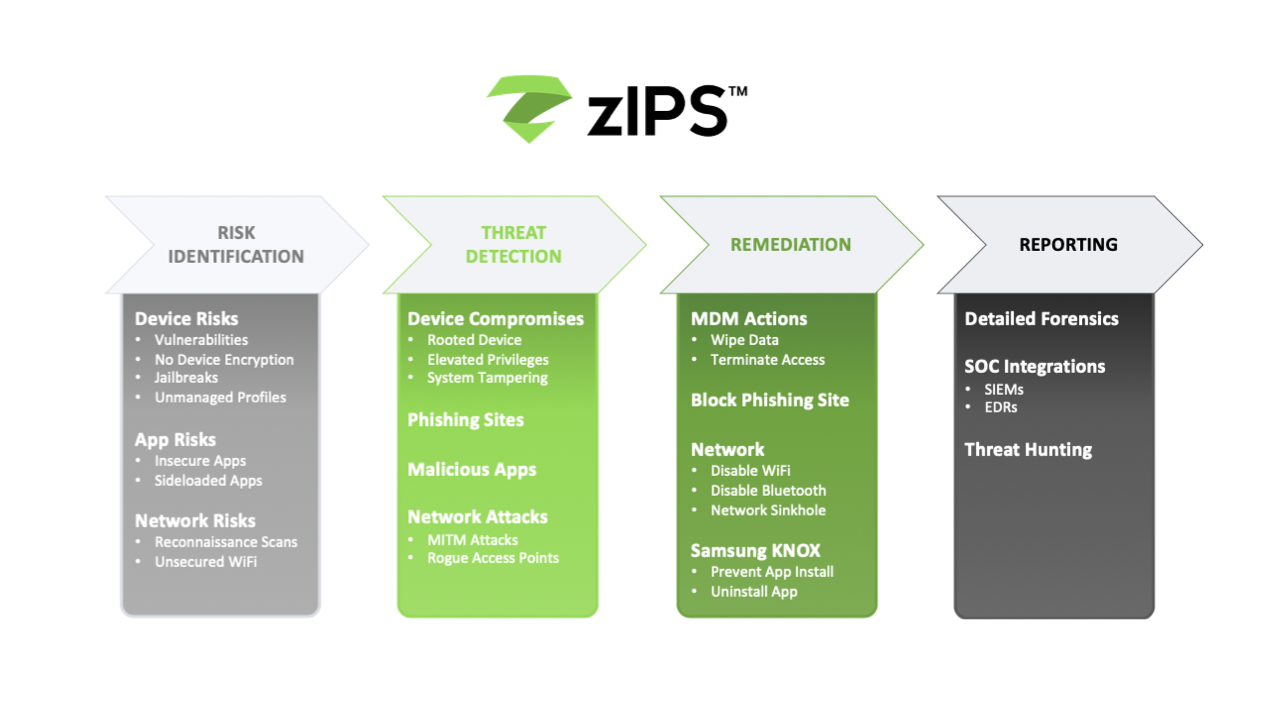 Our zIPS product is the only mobile security solution offering real-time, on-device, machine learning-based detection and protection of known and unknown threats on Android and iOS devices. zIPS runs locally on any mobile device and detects device, network, phishing and malicious app cyberattacks without a connection to the cloud. When it detects suspicious activities on-device, it sends detailed threat forensics data that can be used for SOC analysis.
Our zIPS product is the only mobile security solution offering real-time, on-device, machine learning-based detection and protection of known and unknown threats on Android and iOS devices. zIPS runs locally on any mobile device and detects device, network, phishing and malicious app cyberattacks without a connection to the cloud. When it detects suspicious activities on-device, it sends detailed threat forensics data that can be used for SOC analysis.
4 – Enable BYO use cases with Microsoft Endpoint Manager MAM
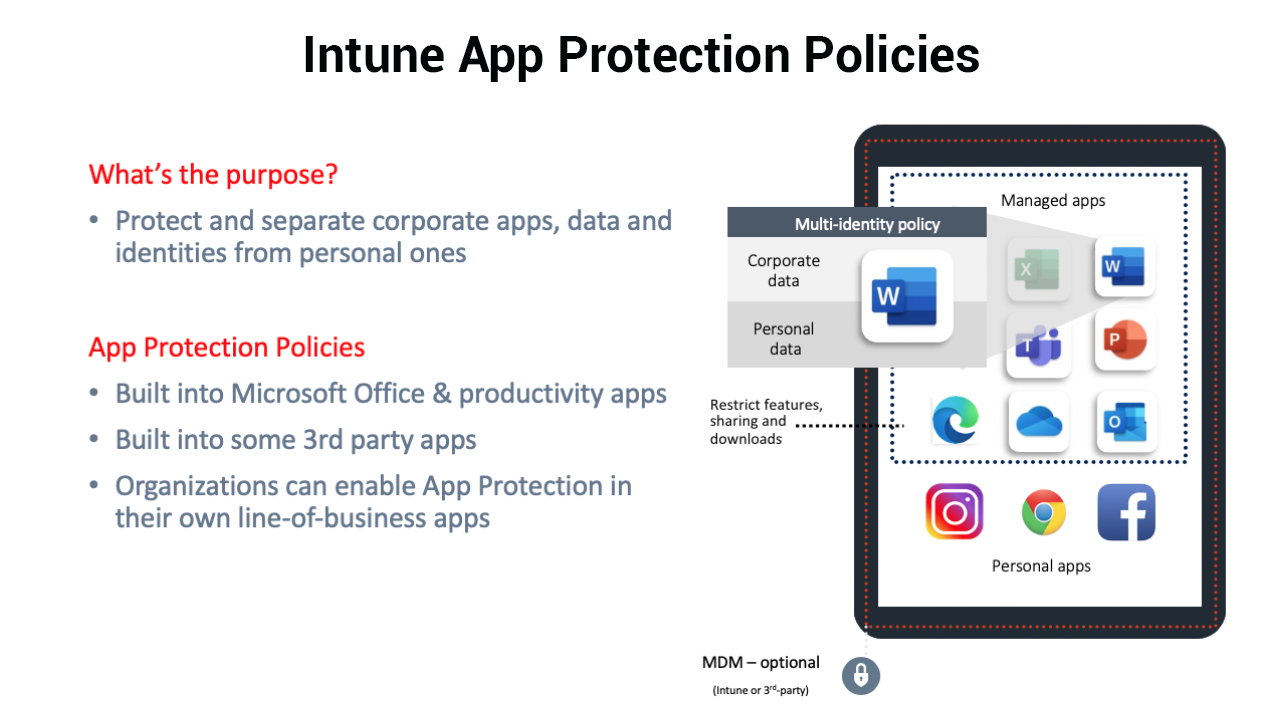
App protection policies are built into all the core Microsoft Office apps, as well as the top 3rd party, and line of business (LOB) apps used for productivity. They are available on iOS and Android; and referred to as Windows Information Protection in the context of Windows. IT admins can configure settings in the areas of data protection, access requirements, and conditional launch.
Data protection settings govern behaviors like data transfer between managed and unmanaged contexts; access requirements specify PIN or corp credential requirements to get into the corporate context of the app; and conditional launch is a set of ‘conditions’ that a device or app must meet in order to allow the end user to get into their corporate data.
Intune’s app protection policies can be used with or without device enrollment into an MDM provider. And one scenario they enable is protection of corp data for organizations with BYOD programs.
5 – Secure BYO endpoints with Zimperium zIPS + Endpoint Manager MAM
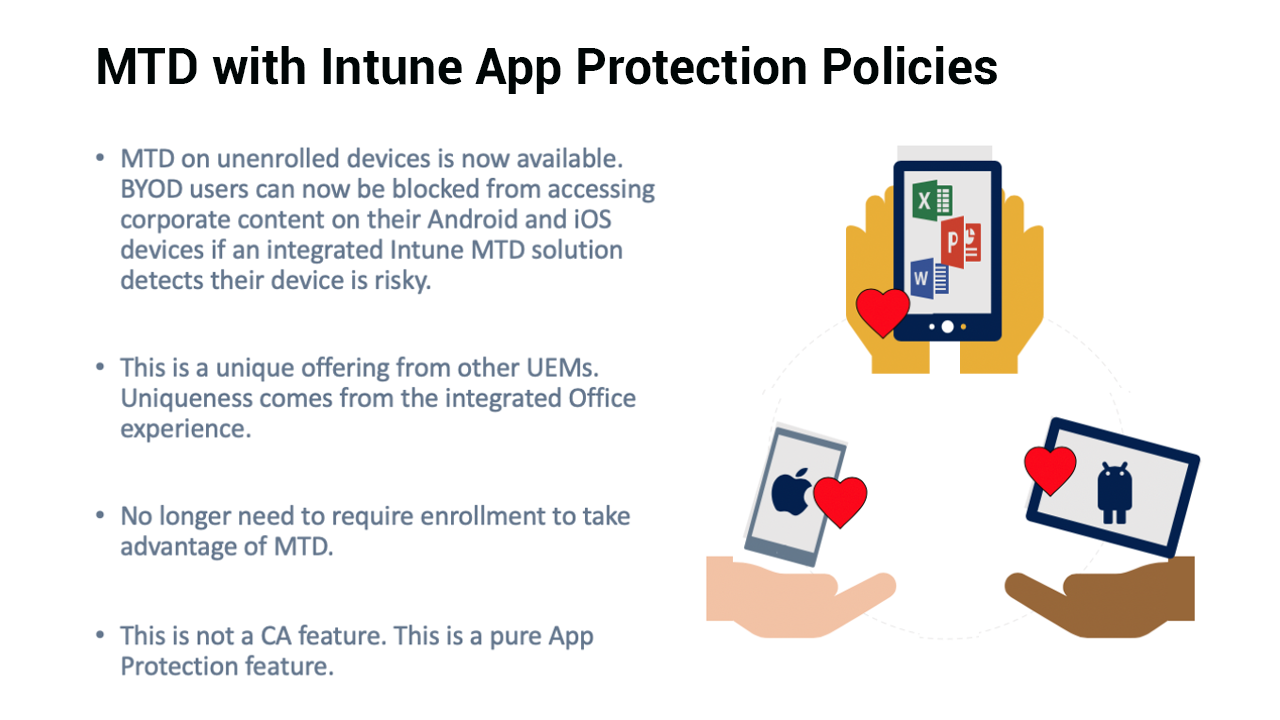
Doing so allows enterprises to detect and remediate any threats while respecting the privacy of its employees.







